In a nutshell
Cyber attackers are focusing on new portfolio companies immediately after deal completion. Why is that happening, and what can we do to guard ourselves against it?
The portfolio is vulnerable
Note, I write this article based on my role as a diligence provider, not a cyber-security expert. Since the pandemic started, cyber has become a significant assessment area and more likely to disrupt or delay deals. From the tech perspective, it’s often more of an issue than the tech itself.
Whether a minor venture/growth deal or a mega corporate takeover, there is a human need to communicate success within the industry. Success is a new deal, of course. But, closing a deal creates the same hope and excitement a salesperson experiences when closing a deal.
When a new client is brought in, rockets go off, bells sound, your name gets in the firm newsletter, and you can bank on a good bonus.
David Maister Managing the Professional Services Firm.
Maister wrote that excellent book back in 1993, but the sentiment is the same for Private Equity deals – we celebrate that new deals are closed, But the problem is that those announcements are leading to cyber attacks.
The types of announcements that are related to new investment deals:
- Media announcements such as Private Equity New’s Deal Page or Pitchbook’s News
- Data platforms such as Crunchbase’s Funding Rounds
- Posts of Private Equity Deals, Awards, Exits and other announcements on LinkedIn
- Professional Services Firms Announcements
- Detailed research papers (Investors love data and benchmarking!) such as Pitchbook’s Private Equity Breakdown reports
- Other Private Equity specific databases such as mergr.com, which we use internally.
- Change of business owners, Directors as on Companies House etc.
This is, of course, not an exhaustive list but shows the effort people put in and the surge of information related to a single deal. Now multiply all that online data and sources, and that’s a pretty good dataset to develop some trend analysis. For example, according to the chart below, there were 592 PE deals in the UK in 2021, and it appears we will beat that number in 2022.
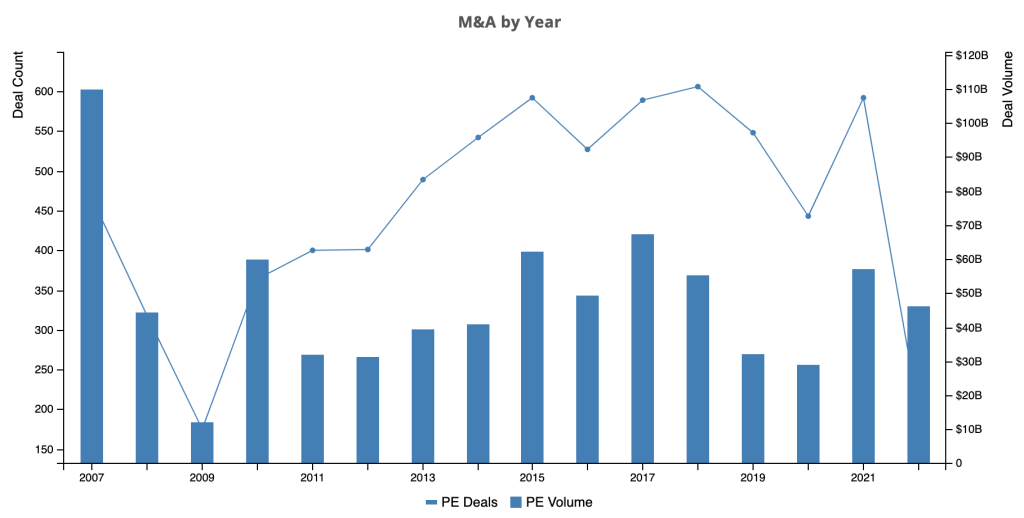
So there’s a perfect data set for nefarious actors to collect information and identify targets to attack. They could combine the announcements data with other products to identify tech stacks and then run small tests against each company to uncover weaknesses. These rich sources of data and what can be learnt from them have a more substantial business case for investment to build a platform than some startups we see.
Consider an alternative perspective.
All of the above, and much more, is a goldmine for a team of Python developers with web-scraping and, dare I use some buzzword bingo, Machine Learning skills. Whilst most of us are using data to create benchmarking and platforms to assess portfolio firms, attackers can use the same approach to create a ‘shadow alternative’.
Using the data they will create methods to identify lesser-known companies and exploit or attack them.
Why are these deals of particular interest to attackers?
‘Private Equity backed’ is a more alluring career choice (even for attackers)
Working for PE-backed firms has become more popular, especially for senior roles. I think it’s due to the creativity possible in an organisation with new backing, objectives, and an aggressive growth plan. There are more ‘Getting into PE’ networking events and, of course, many Podcast interviews of tech leaders’ experiences in PE. Martha Heller sums it up nicely in her article explaining why Private Equity needs CIO expertise:
I have always loved the “CIO turned private equity executive” career trajectory, as it has all the diversity of consulting, but from the vantage point of an investor.
Martha Heller,CIO.COM
We can assume that where tech leadership goes, their shadow – the cyber attackers – follows. As more tech leaders strive to move into and scale PE-backed firms, so will their attackers.
And whilst The type of buyer impacts your Tech DD, if it’s a trade buyer, they will not want additional cyber risks if they are to integrate your business and technology into their environment.
Management is exhausted
Well, if they’ve just closed a private equity deal, then it’s likely that management has been focused on due diligence for at least a few months. During this time it’s likely their eyes won’t be entirely on the ball, and vulnerabilities seep in. It’s unusual to hire extra people for due diligence (maybe the odd CFO here and there), so it’s the same workforce now having to undertake considerable work.
At deal close, management has been keeping the lights on (at best) and working into the early hours to answer information requests. At deal close, they are exhausted and maybe the business and underlying tech. As a result of all the exhaustion and lack of eyes on the ball, it potentially leaves the business vulnerable to attack or something along those lines.
This is ironic considering the intention of the DD exercise, which is partly to confirm the business tech is fit for sale.
New ownership
There’s no rest for the wicked. Immediately after the deal closes, the next critical milestone for tech leadership (and management in general) is the first board meeting. That may only be weeks away, but it’s the first opportunity to present substantive detail against what was promised during the due diligence exercise.
There may be new players to contend with, such as board members and new partners to meet to help quickly ramp up to what will become the ‘new normal’ for both pace and decision-making. So there is a chance that management goes from being exhausted from ‘deal fatigue’ to working at a newer pace with new reporting methods. That isn’t an issue, and all teams adapt to the new world. Still, there is a period of vulnerability for a few weeks as the focus is again distracted away from the core business. Hence there is a window of time where the company continues to be more vulnerable to cyber attacks.
Saving face
And speaking to portfolio firms that have experienced cyber attacks post-deal, they recall it being a difficult period of change. Neither the investor nor management want this to happen on their watch, and it’s not exactly the best thing to be presented in the early board meetings. This risk of making the business more vulnerable wasn’t on the business plan discussed during due diligence (see remedies section), nor does it look good to anyone with a vested interest.
The problem needs dealing with quickly, which might mean taking action that management would usually avoid, such as paying ransomware demands. But, on a more positive note, this may be the first ‘major issue’ the new partners have worked on and may bring them closer together.
Evidence of Post-Deal Cyber Attacks
My evidence is speaking to existing and new customers, those that have experienced this difficult and embarrassing issue of being attacked post deal. I also spent 25+ years working in M&A post-merger integration roles and projects and noticed how people in tech teams would temporarily relax security to enable a critical business change. Still, they don’t keep track of those ‘allowances’ and often forget to switch the security back on. In that situation, the CISO isn’t usually aware nor tech management.
Not having the resources and marketing budget of a Big4, I refer you to this report written by Deloitte titled ‘The Role of Cyber Security in M&A‘.
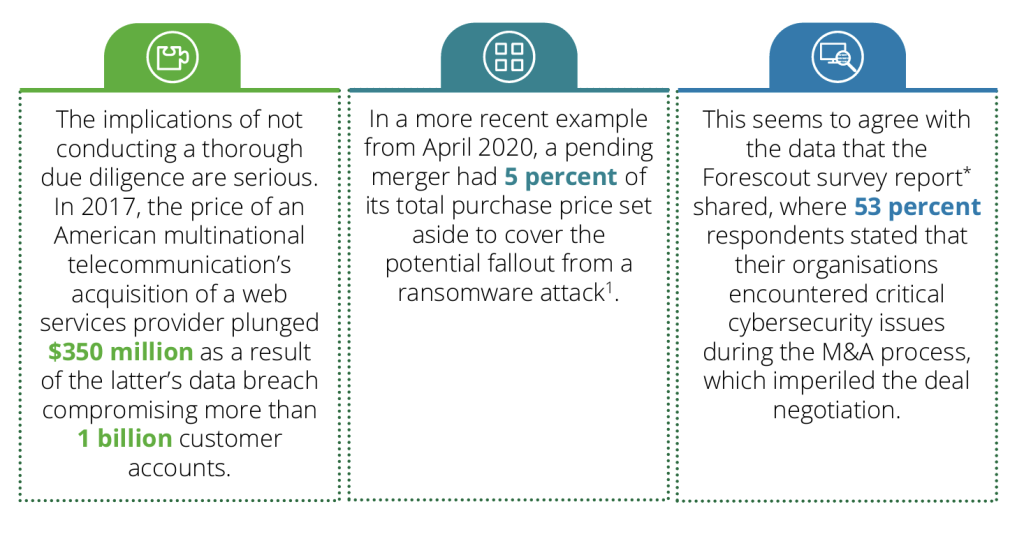
I don’t have access to the data that support this statement below. Still, it is relevant to my argument even if the article refers to mega M&A deals with the significant Tech acquirers (e.g. Microsoft and Alphabet) with whom we don’t get involved:
An unprecedented surge in ransomware, software vulnerabilities and malign cyber activity against the private sector and critical infrastructure has led to a wave of private equity investment and merger activity in the cybersecurity industry.
David Jones, M&A sets record pace as ransomware, nation-state threats fuel security demand
Solution
Please remember my suggestions are based on common issues and practices we tend to see during technology due diligence – not from a cyber security strategic perspective. Below are some remedies that may help a portfolio firm prepare its security before a deal is closed:
Fix Back Office IT
If Back Office IT ‘red flags’ are highlighted during tech due diligence, seriously consider addressing them before the deal completes. This is mainly a concern for SaaS companies, even if they are mature and have a ‘corporate IT’ function. A common issue is that the back office IT has been neglected in favour of the revenue-generating systems.
Fair cop, until there’s a new deal.
It can be obvious issues such as a lack of a central domain, central management, use of own devices, people buying their own devices etc. However, so many concerns can appear that are too many to list here.
There will be little interest in investing pre-deal as this may impact the focus of the team, disrupt the day-to-day operations when the business needs to appear as stable as possible, and, of course, the expense. But what about the pain and disruption if the target business is attacked soon after the deal?
Local Admins
A low-tech solution is to ensure employees, including software developers, do not have ‘local administrator’ access to their computers. I am writing this simplistically to say that not having local admin also means you cannot ‘install’ viruses. This is not interesting to an investor and possibly ‘old news’ to a tech leader. Still, this simple measure which has been around for years can be enabled before the deal completes and stop specific attacks from propagating across the team. Unfortunately, it is also a political issue within firms and often isn’t enabled for software developers.
Don’t mark your own homework
As a firm grows, incumbent management takes on new responsibilities – such as cyber security (and GDPR). This keeps the costs down, reduces politics, keeps cadence high etc. But if the person that is pushing and instigating change is also the person that is responsible for cyber security, then there might be an issue as there is nobody to challenge the status quo.
Resolving this conflict of interest does not mean hiring an expensive FTE. On the contrary, there are many ways to address this while keeping costs down and assuring investors. But pre-deal (or even pre-Tech DD engagement), it would be good to consider engaging a Security SME to review and provide recommendations.
Consider new tools and methods
The target firm may have bad habits that have developed over the years and are not a concern when running privately or under the radar of current investors. For example, sending emails with personal or financial data might have been happening for years, baked in as a long-term business process.
Even if it’s a longstanding process, it doesn’t mean it’s right.
Tools exist to help control data flow inside and outside the firm. Other tools help identify when intruders are trying to access systems. I am not stating they need to be implemented before the deal closes. Still, these tools may already be available to the target firm as part of their existing back office IT tools, and it’s worth having a dig around to see what could be enabled to protect the business.
Patching (updating) systems and code
Update systems to keep them secure. The problem is if the firm hasn’t done this for a while (which, in some cases, could be many years). If not all systems are up to date, of course, work out why, and also if they can be updated. This also means keeping an eye on code and possible vulnerabilities. It’s a complex subject, but a simple question of asking the target about their software and back office patching status should help kick this into gear.
Watch out for ‘easy’ ISO audits
Don’t assume that if a firm has ISO certifications, it is secure.
Working for three portfolio firms that made a ton of acquisitions of smaller companies uncovered a trend for those firms to acquire ISO certifications which were more paper qualifications. Hence they had decent paper policies but were not very secure. One acquirer we worked with coined the term ‘easy auditors’ to represent the firms with ISO certifications and low-security measures. Buyer, beware.
Ensure the target is prepared for the announcements
If the deal goes through, ensure the Operations teams are versed at the correct time and enough time is provided to shore up the environment for any attacks. Ask the team to plug any known security gaps because unwanted parties may uncover those gaps.
Use the tools you pay for
Many teams build up an array of security tools and platforms as they evolve. Some check the code, the networks, infrastructure etc. and during Tech Due Diligence, we often uncover that said tools are not configured correctly or are only half-configured. These tools often give a false sense of security, but it’s an easy thing to check and remedy.
Take action on the data
If security tools are in place and correctly configured, another area the portfolio can focus on is taking action on recommendations highlighted through the tools, pentests etc. Again, it’s our job to review said information and provide opinions, but the target’s team’s responsibility is to address issues that are ‘known’ yet previously deemed as non-critical.
Reassure the Team
Left to last as this recommendation is a post-deal concern but added here for completeness.
There needs to be an assurance that increasing security measures do not necessarily have to impact the delivery cadence. Done right, you have both ‘secure’ and ‘speed’. I always try and avoid quoting the major Tech players as case studies because it usually results in the response of ‘yes, but they have more budget and resources.
But I cannot resist here, as Archie Cowan’s article points out (and then breaks it down to engineer level) that Amazon deploys 50m changes a year. But to be more helpful, we’re seeing much smaller firms with limited resources managing 500-1,000 secure deployments a year with 10-20 staff. Again, I am not writing to debate what’s a good number of deployments per team or engineer, as the relevance of this is dependent on your user’s needs. Some firms moved back from daily to quarterly releases as they have Enterprise customers who prefer not to opt-in to rapid change.
The key is that the team may have to learn and change their behaviour, and there may be a dip in how often in the short term.
Conclusion
I am not trying to sell ‘project fear’ here, nor am I selling the need for cyber security assessments. I am sharing this observation for awareness and debate. Often portfolio firms can reconfigure their systems without major additional costs or re-focus the team on areas they already are aware are cyber security concerns.







